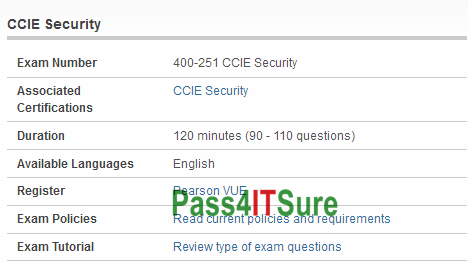
What’s new with Cisco 400-251 dumps? The CCIE Security Written Exam (v5.0) (400-251 CCIE Security) exam is a 120 minutes (90 – 110 questions) assessment in pass4itsure that is associated with the CCIE Security certification. 100% pass guarantee Cisco CCIE Security 400-251 dumps exam Youtube study guide guaranteed success. “CCIE Security Written Exam (v5.0)” is the exam name of Pass4itsure Cisco 400-251 dumps test which designed to help candidates prepare for and pass the Cisco 400-251 exam.
We prepare the best study guide and the best online service specifically for IT professionals to provide a shortcut. Cisco CCIE Security https://www.pass4itsure.com/400-251.html dumps CCIE Security exam latest dumps of Pass4itsure, you know this is something you do everything possible to want, and it is really perfect for the exam preparation.
[Updated December 2017 Cisco 400-251 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWN3NKQ2VvYmxCMDg
[Updated December 2017 Cisco 210-065 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWQk1xeU5TZ3ExalE
QUESTION 110
What are the two technologies that support AFT? (Choose two)
A. NAT-PT
B. SNAT
C. NAT64
D. DNAT
E. NAT-PMP
F. NAT-6to4
400-251 exam Correct Answer: AC
QUESTION 111
According to RFC 4890, which three message must be dropped at the transit firewall/router?(Choose three.)
A. Router Renumbering(Type 138)
B. Node Information Query(Type 139)
C. Router Solicitation(Type 133)
D. Node information Response(Type
E. Router Advertisement(Type 134)
F. Neighbor Solicitation(Type 135)
Correct Answer: ABD
QUESTION 112
Which two options are disadvantages of MPLS layers 3 VPN services? (choose two)
A. They requires cooperation with the service provider to implement transport of non-IP traffic.
B. SLAs are not supported by the service provider.
C. It requires customers to implement QoS to manage congestion in the network.
D. Integration between Layers 2 and 3 peering services is not supported.
E. They may be limited by the technology offered by the service provider.
F. They can transport only IPv6 routing traffic.
400-251 dumps Correct Answer: DE
QUESTION 113
From the list below, which one is the major benefit of AMP Threat GRID?
A. AMP Threat Grid collects file information from customer servers and run tests on them to see if they are infected with viruses
B. AMP Threat Grid learns ONLY from data you pass on your network and not from anything else to monitor for suspicious behavior. This makes the system much faster and efficient
C. AMP Threat Grid combines Static, and Dynamic Malware analysis with threat intelligence into one combined solution
D. AMP Threat Grid analyzes suspicious behavior in your network against exactly 400 behavioral indicators
Correct Answer: C
QUESTION 114
Which statement best describes the concepts of rootkits and privilege escalation?
A. Rootkits propagate themselves.
B. Privilege escalation is the result of a rootkit.
C. Rootkits are a result of a privilege escalation.
D. Both of these require a TCP port to gain access.
400-251 pdf Correct Answer: B
QUESTION 115
Which two statements about PVLAN port types are true ? (Choose two)
A. A promiscuous port can send traffic to all ports within a broadcast domain
B. An isolated port can receive traffic t from promiscuous ports in any community on its Broadcast domain, but can send traffic only to ports in its own community
C. An isolated port can send and receive traffic only to and from promiscuous ports
D. A community port can send traffic to promiscuous ports in other communities its Broadcast domain
E. A community port can send traffic to community ports in other communities its Broadcast domain
F. A promiscuous can send traffic to to community ports in other Broadcast domainS
Correct Answer: AC
QUESTION 116
On an ASA firewall in multiple context mode running version 8.X, what is the default number of VPN site to-site tunnels per context?
A. 2 sessions
B. 4 sessions
C. 1 session
D. 0 sessions
400-251 vce Correct Answer: A
QUESTION 117
Which two options describe the main purpose of EIGRP authentication?(Choose two)
A. to allow faster convergence
B. to identify authorized peers
C. to provide redundancy
D. to provide routing updates confidentiality
E. to prevent injection of incorrect routing information
Correct Answer: BE
QUESTION 118
In a Cisco ASA multiple-context mode of operation configuration ,what three session types are resource limited by default when their context is a member of the default class?(Choose three)
A. ASDM sessions
B. Telnet sessions
C. IPSec sessions
D. SSL VPN sessions
E. TCP sessions
F. SSH sessions
400-251 exam Correct Answer: ABF
QUESTION NO: 119
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. The application rarely experiences errors that cannot be reproduced on a test environment. You are required to ensure that the application meets the following requirements:
l All unanticipated errors are logged.
l Logging is configured with a least amount of alteration to the application code. What will you do?
A. Override the base class for all forms in the application to add the Try/Catch blocks to all the major functionalities.
B. Enable the <customErrors> element in the Web.config file and set the mode attribute to On .
C. Enable the <customErrors> element in the Web.config file and set the mode attribute to RemoteOnly.
D. Add an event handler for the Application.Error event to the Global.asax file of the applicatio n.
Answer: D
QUESTION NO: 120
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You have recently finished the development of an ASP.NET Web application using .NET Framework 3.5. The application must be deployed by using the The application has several Web forms. You need to implement Really Simple Syndication (RSS) feeds functionality. The RSS feeds will be used by the You must ensure that the application displays the RSS-formatted information when accessing the given URL. What will you do to accomplish this? Each correct answer represents a part of the solution. Choose two.
A. Create and register a custom HttpHandler class that releases the RSS feeds.
B. Create a Web form named Updates that releases the RSS feeds.
C. Create an ASMX Web service component named Updates.
D. Add the HttpHandler class to the .rss extension.
E. Create and register a custom HttpModule class.
400-251 dumps Answer: A,D
QUESTION NO: 121
You work as an Enterprise Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. You want to notify the users when a print job has finished. Which of the following events will you use to accomplish the task?
A. PrintDocument.PrintPage
B. PrintDocument.EndPrint
C. PrintDocument.QueryPageSettings
D. PrintDocument.BeginPrint
Answer: B
QUESTION NO: 122
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You create a Web service using .NET Framework 2.0. You want the Web service to utilize a two step process to map XML generated by Web methods to .NET objects. What will you do to accomplish the task? Each correct answer represents a part of the solution. Choose two.
A. Use deserialization
B. Use serialization
C. Use Marshal-by-ref objects
D. Use Marshal-by-value objects
400-251 pdf Answer: A,B
QUESTION NO: 123
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished development of Web services using the .NET Framework. The access control to Web services is part of your accountability. You are currently revealing an existing class as a XML Web service. You are required to ensure that the XML Web service is exclusively accessible to Web service clients within the ABC Inc. domain. To fulfill this requirement you want to change the access modifiers on methods that must be represented as Web methods. What will you do to accomplish this task?
A. Use the Public access modifier for each Web method.
B. Use the Private access modifier for each Web method.
C. Use the Internal or Friend access modifier for each Web method.
D. Use the Protected access modifier for each Web method.
Answer: A
QUESTION NO: 124
You work as a Web Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Web application using .NET Framework 2.0. You add a Web Form that contains a button named bCancel. The button allows users to exit the form. When users click the button, validation should not occur. However, during testing you find that clicking the button does not allow users to exit the form. You need to ensure that users can always exit the page. What will you do?
A. Set the CausesValidation property of the bCancel button to false.
B. Set the AccessibleName property of the validation controls on the Web Form to “false”.
C. Set the ControlToValidate property of the validation controls on the Web Form to the ID of the control.
D. Set the Enabled property of the validation controls on the Web Form to false.
400-251 vce Answer: A
QUESTION NO: 125
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You are creating an ASP.NET Web application using the .NET Framework 3.5. The application stores sensitive profile data in a MS SQL Server 2008 database. You are required to make sure that the profile data never stored in clear text. What will you do?
A. Create a strongly typed custom ProfileProvider class. In the ProfileProvider class, encrypt the provided information before storing it in the database.
B. Use the ASP.NET IIS Registration Tool to encrypt the connection string to connect to the SQL Server database.
C. Create a custom profile provider. In the custom provider, encrypt the provided information before storing it in the database.
D. Enable the SSL encryption for the SQL Server connections.
Answer: C
QUESTION NO: 126
Allen works as a Software Developer for ManSoft Inc. He develops an application using Visual Studio .NET 2005. Only the employees of the company use the application. Allen wants to ensure that when a request on a page is made by a user the application asks for his authentication. Which of the following actions will Allen take to accomplish the task? Each correct answer represents a part of the solution. Choose two.
A. Specify User.Identity to authenticate the user.
B. Set the impersonate attribute of the <identity> element to true.
C. Specify the username and password attributes.
D. Set the impersonate attribute of the <identity> element to false.
400-251 exam Answer: B,C
QUESTION NO: 127
George works as a Software Developer for GenTech Inc. He creates an application named App1 using Visual Studio .NET. App1 uses the version 2.0.0.0 of an assembly named Assembly1. However, he wants App1 to use a new version i.e. 2.1.0.0 of Assembly1. Therefore, he needs to specify Assembly1’s location so that App1 can use version 2.1.0.0 of Assembly1. What will
George use to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.
A. An unmanaged code.
B. A managed code.
C. The <probing> element.
D. The <codeBase> element.
Answer: C,D
QUESTION NO: 128
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be deployed on an intranet server of the company. You require that the application meets the following requirements:
l Users can log on to the application by using their Active Directory credentials.
l Each Web page in the application must display user name and password controls for an unauthenticated user.
What will you do to accomplish this?
A. Use Forms authentication and use the SqlMembershipProvider class.
B. Use Forms authentication and use the ActiveDirectoryMembershipProvider class.
C. Use Windows authentication and enable impersonation.
D. Use Windows authentication and disable impersonation.
400-251 dumps Answer: B
QUESTION NO: 129
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using .NET Framework. He wants to encrypt all his e-mails that he sends to anyone. Which of the following will he use to accomplish the task?
A. PPP
B. PPTP
C. FTP
D. PGP
Answer: D

Cisco 400-251 dumps exam is an popular examination of the IT industry , and it is also very important. “CCIE Security Written Exam (v5.0)”, also known as 400-251 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 400-251 dumps exam questions answers are updated (520 Q&As) are verified by experts. The associated certifications of 400-251 dumps is CCIE Security. Pass4itsure Cisco CCIE Security https://www.pass4itsure.com/400-251.html dumps CCIE Security exam latest dumps covers all the content of the examination and answers you need to know.
Cisco 400-251 Dumps Youtube: https://youtu.be/YbeaZVr6TIo